who am i


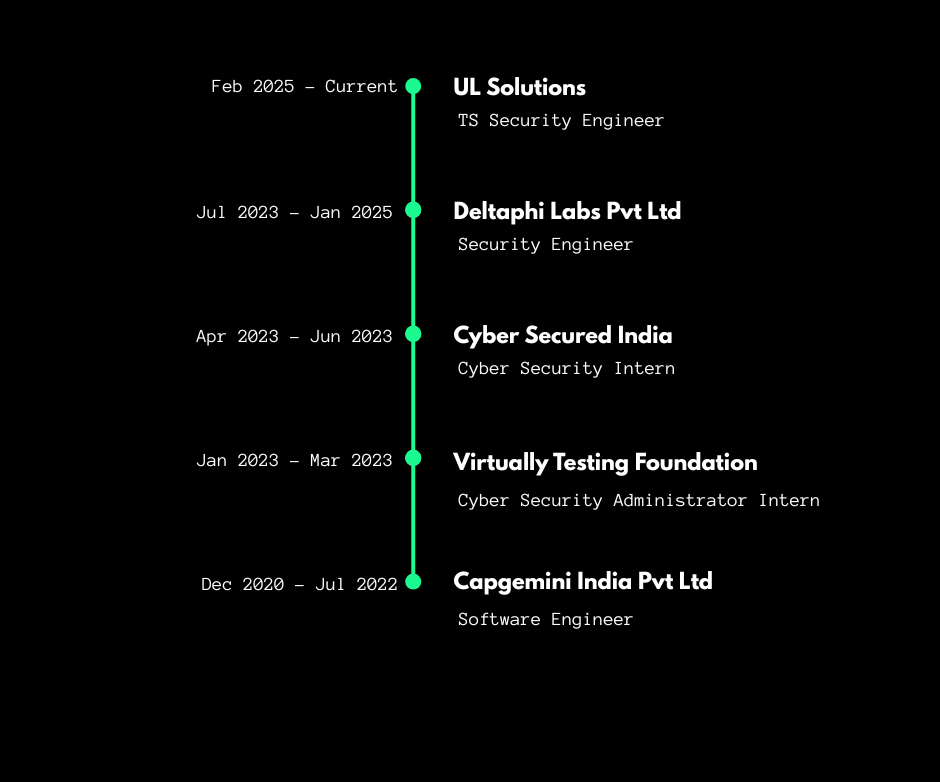
Hi, I am a Security Engineer who loves breaking things so they can be rebuilt safer. Most days you will find me deep in hunting down sneaky auth bugs, path traversal quirks, and those “how is this leaking?” info disclosure issues then turning the fixes into clean, reproducible steps the whole team can use. I started in software, moved into cybersecurity and now split time between web app pentesting, network security testing and ITSAR compliance checks.
I am also building a no-fluff cybersecurity YouTube channel: practical exploit walkthroughs, simple visuals and real-world tips you can try right away. If you like straight talk, clear demos and a bit of curiosity-driven fun, you will feel at home with my content. Outside of client work, I sharpen skills with CTFs and bug bounty-style practice and I am big on making complex topics feel simple.